
Kerberos Authentication Axway Documentation
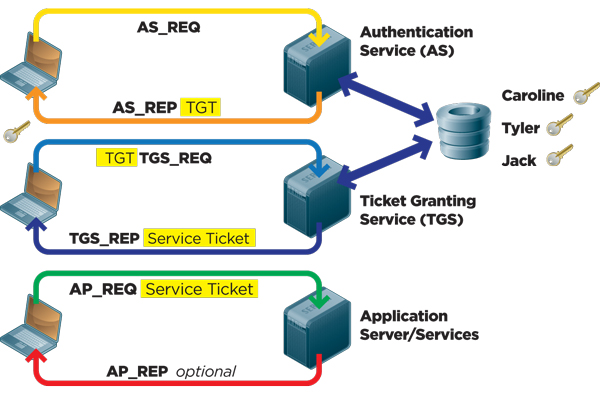

Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
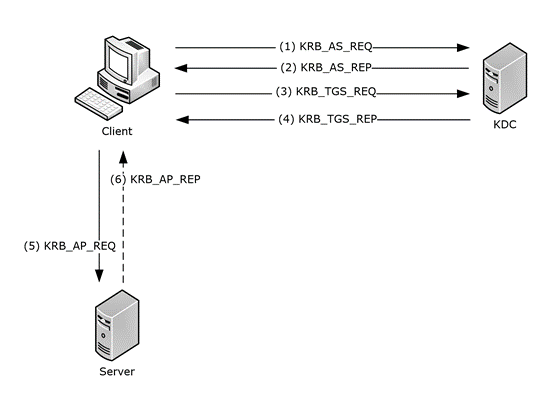
Ms Kile Kerberos Network Authentication Service V5 Synopsis Microsoft Docs
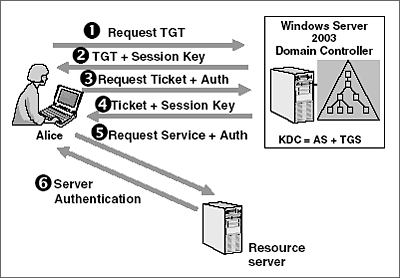
Five Steps To Using The Kerberos Protocol
0 Response to "Kerberos Is Best Described as a Protocol for Authentication"
Post a Comment